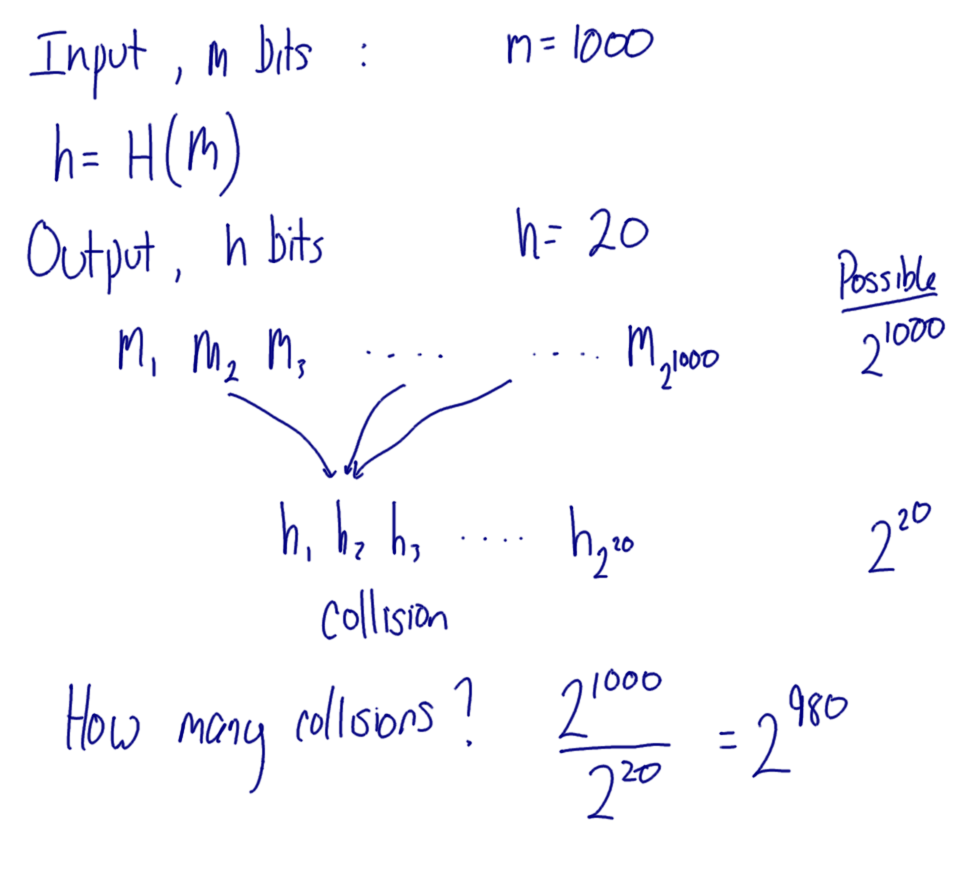
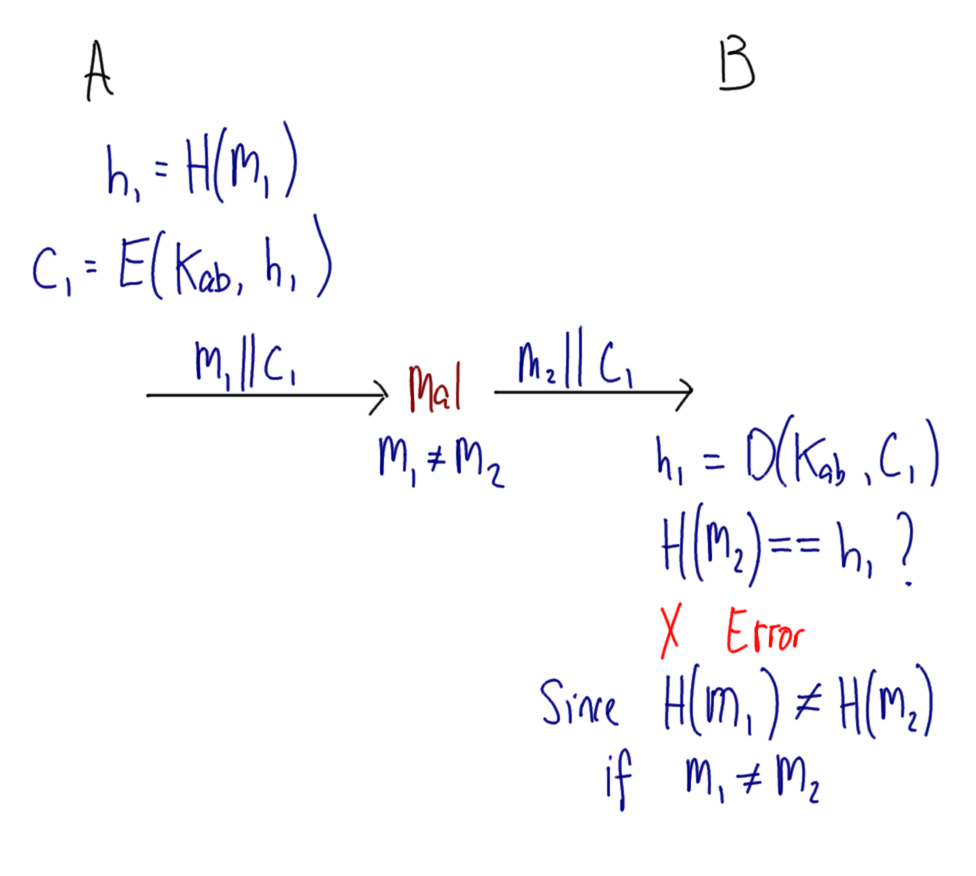
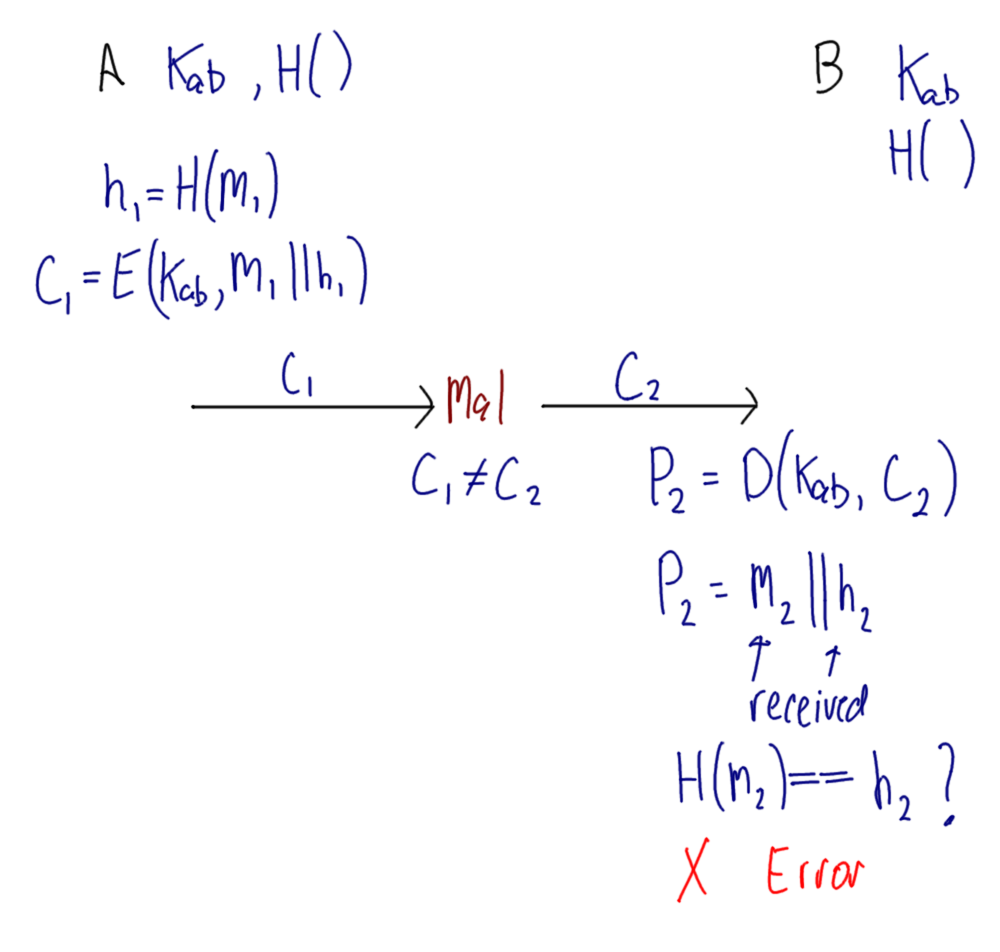
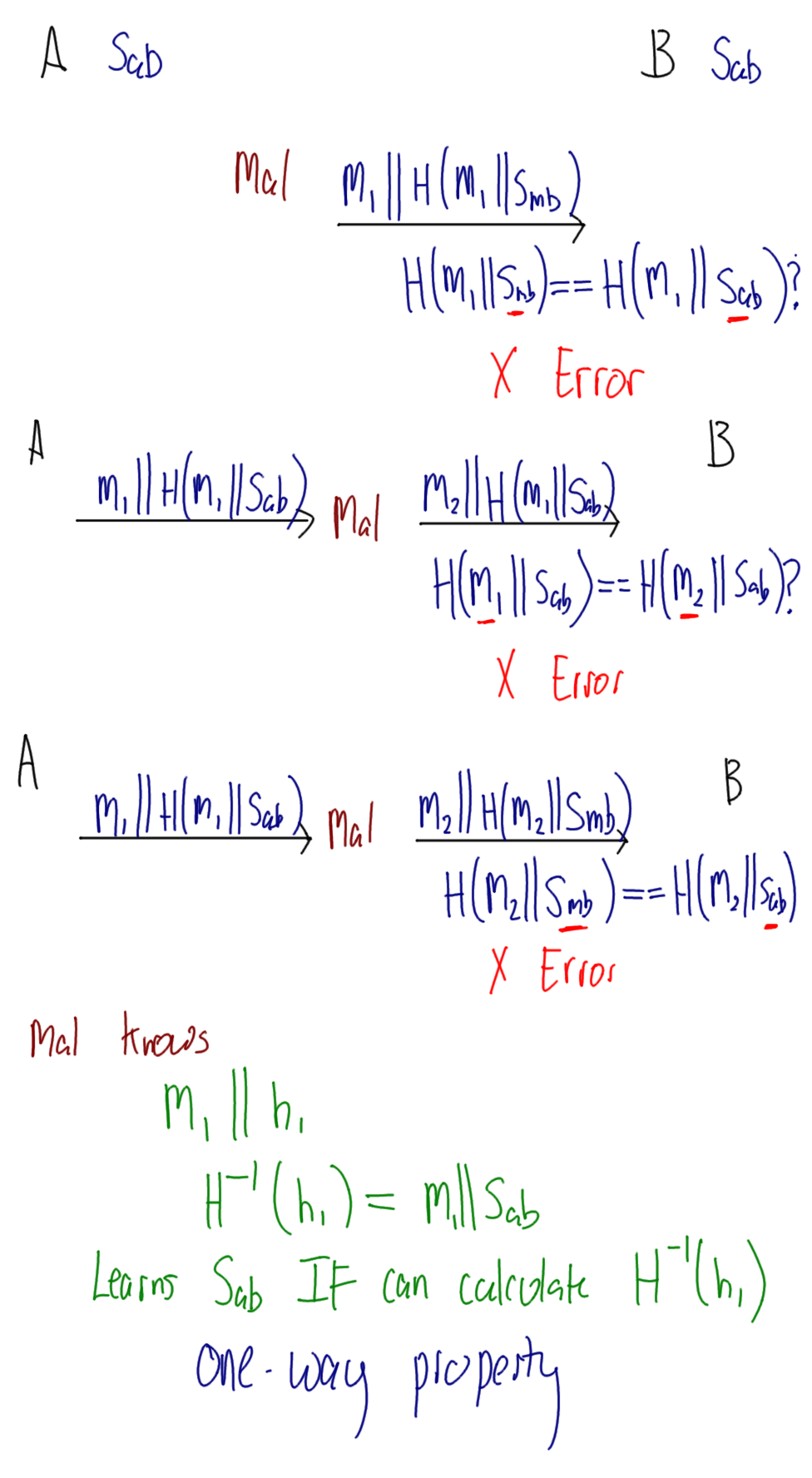
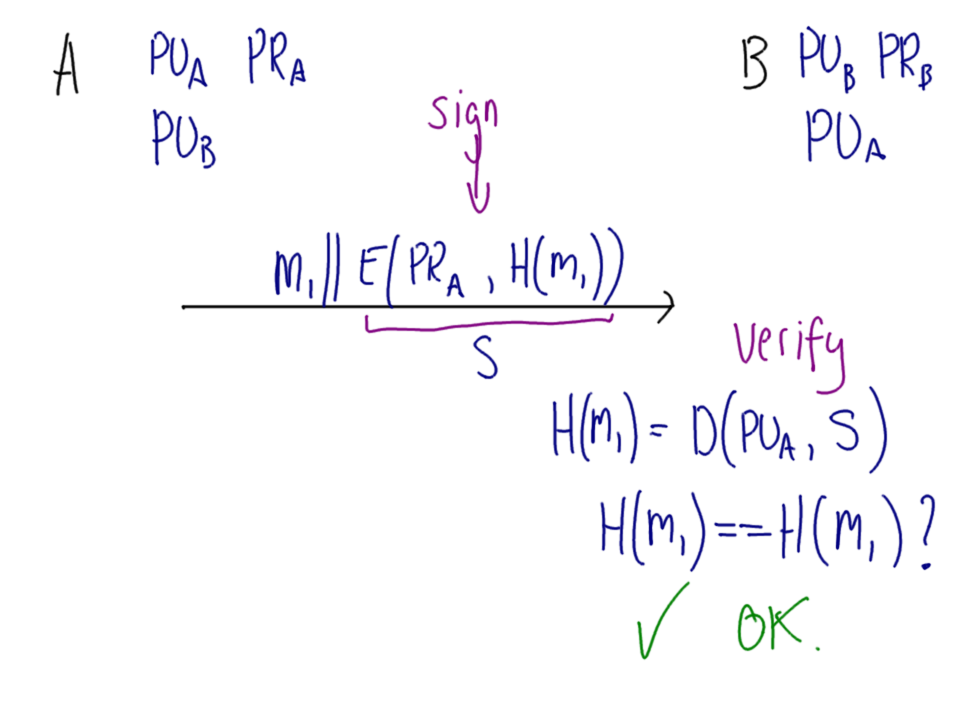
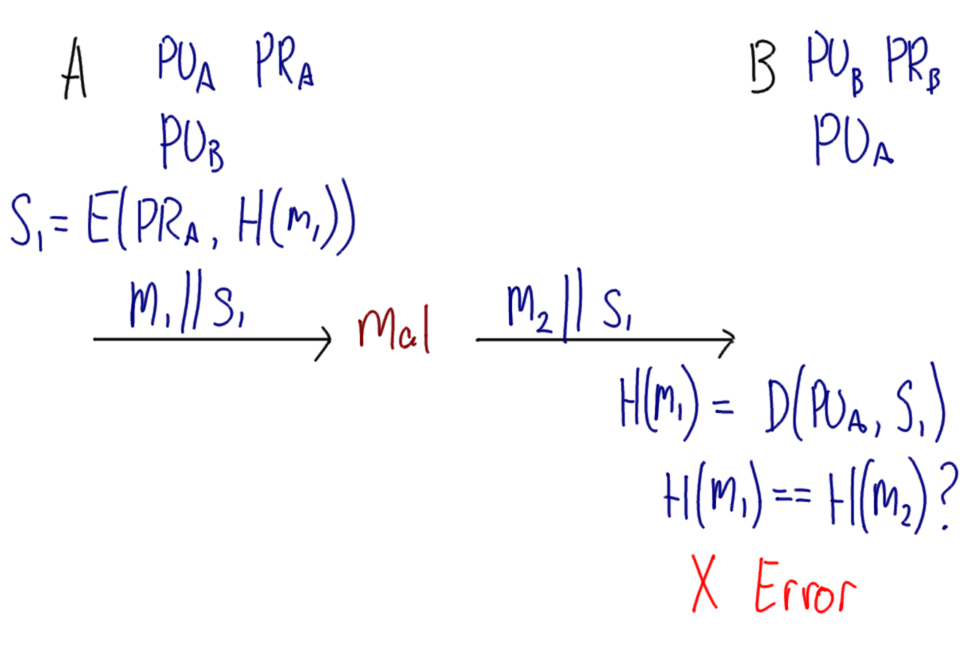
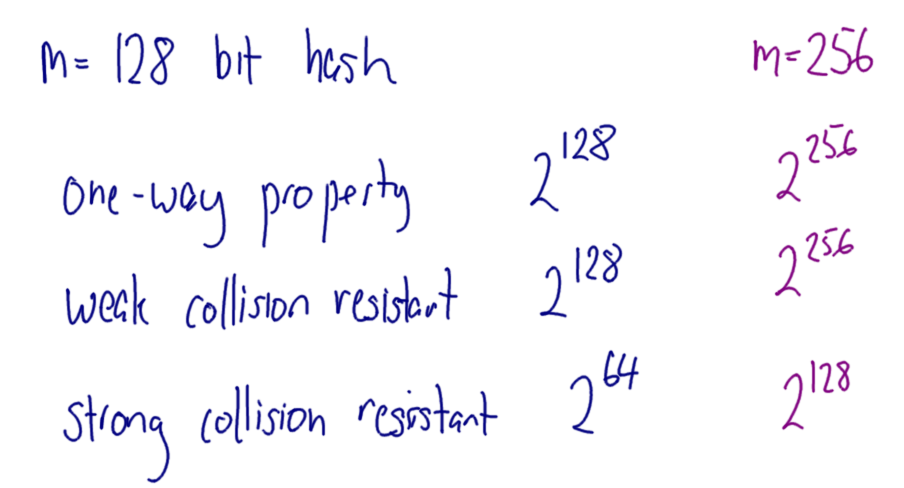
Hover over images to see the title; right-click and view the image to zoom in. Alternatively, download a zip archive with all the images or a printable PDF of the notes. You can also download a printable PDF of the notes from last year.
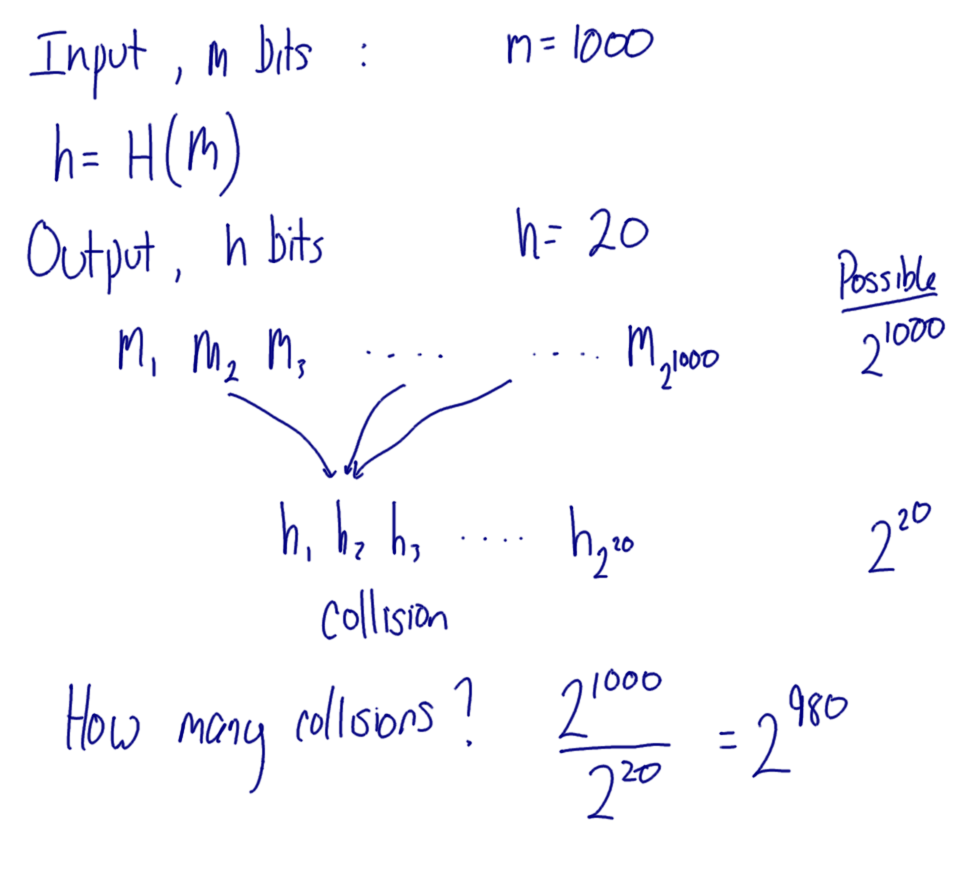
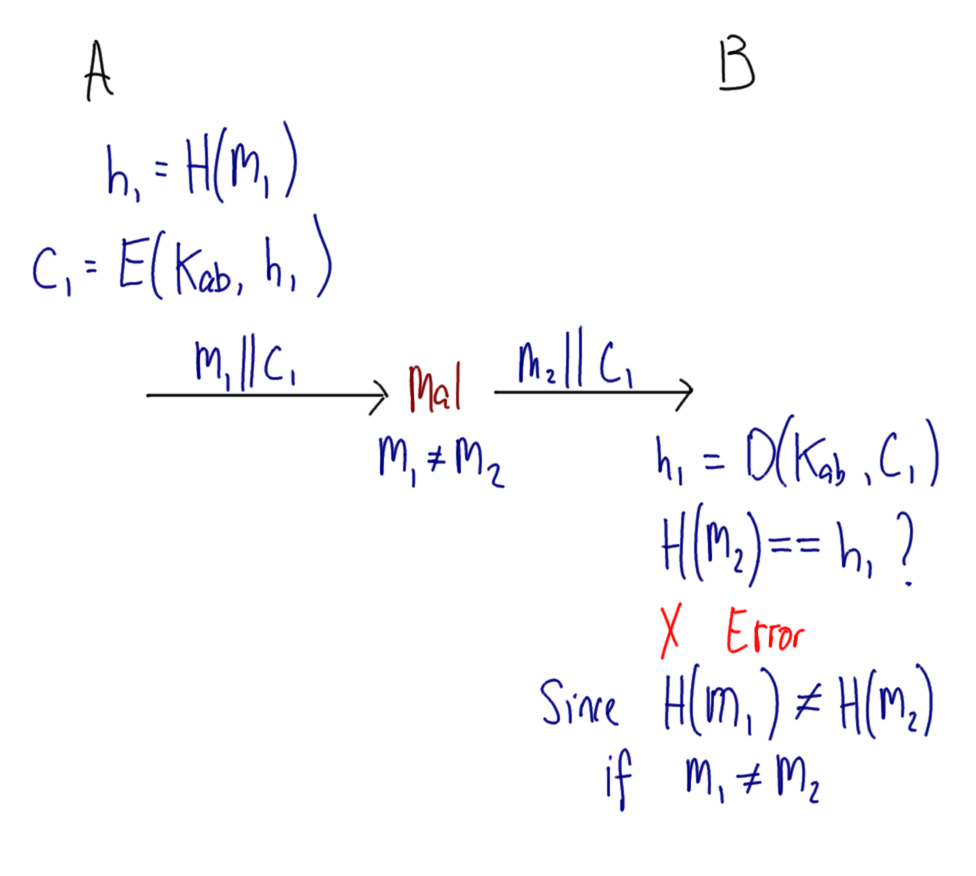



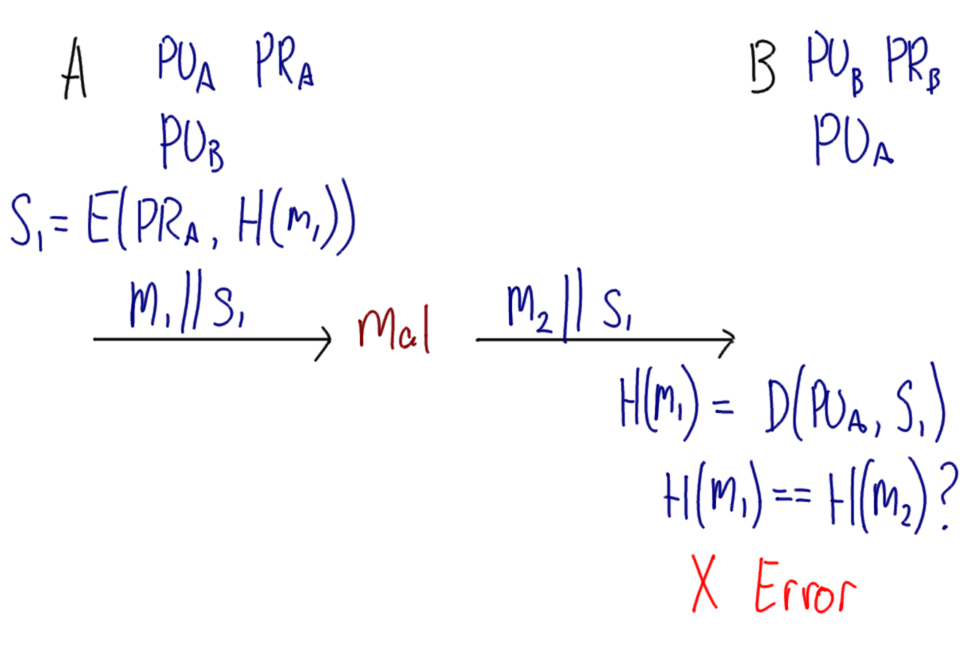
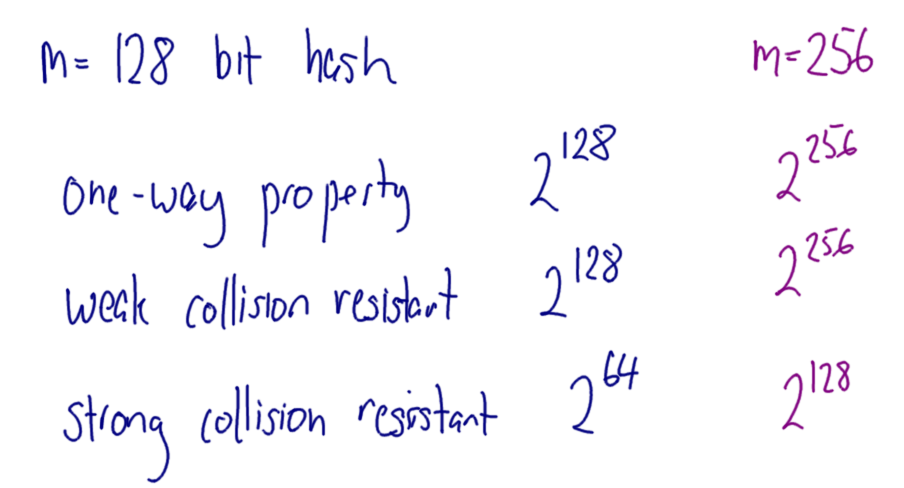
Return to: Course Home | Course List | Steven Gordon's Home | SIIT