Chapter 18
Key Distribution and Management
To be completed in the future.
18.1 Recommended Key Sizes
Users of cryptographic systems need to know what algorithms and parameters that should use, without having to understand the details.
- Various governments, standardisation organisations and researchers have analysed security level of cryptographic mechanisms
- Provide recommendations for:
- Ciphers to use
- Key lengths or hash lengths
- Security level
- BlueKrypt website summarises recommendations: www.keylength.com
- E.g. from NIST, German BSI, NSA, ECRYPT project, …
- ECRYPT-CSA Project 2018 report on Algorithms, Key Size and Protocols (PDF)
The BlueKrypt website summarises recommendations from various organisations. You should visit the website and explore the different recommendations. While there are differences, you can get an approximate idea of the key lengths that should be used.
The ECRYPT-CSA project is one effort to compare algorithms. The PDF report gives a comprehensive summary of different cryptographic mechanisms, analysis of specific algorithms, and recommendations.
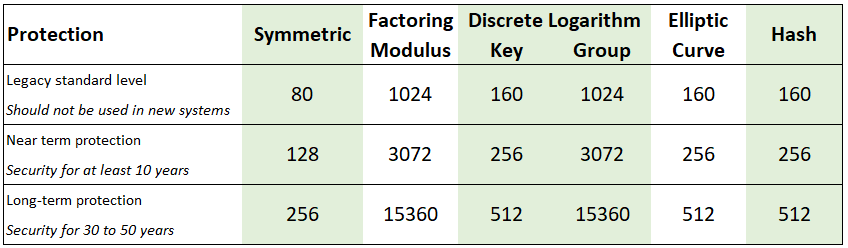 Credit: BlueKrypt www.keylength.com, CC-BY-SA 3.0
Credit: BlueKrypt www.keylength.com, CC-BY-SA 3.0
Figure 18.1 shows recommended key (or hash) lengths, in bits, for symmetric key algorithms (e.g. AES), public key algorithms based on factoring a modulus (e.g. RSA), public key algorithms based on solving discrete logarithms (e.g. the secret key and modulus/group length in Diffie-Hellman), public key algorithms based on elliptic curve cryptography, and hash functions.
Three different levels of security are given: legacy, current (near-term) and future (long-term). Current or future levels of security should be used, although legacy levels may still be secure for some cases.