Chapter 2
Cryptography Concepts and Terminology
File: crypto/concepts.tex, r1961
This chapter defines key concepts and terminology in cryptography. This would likely to have been already covered in a subject that introduces computer security (e.g. an introduction to networking or IT security). Therefore it is quite brief, serving mainly a refresher and to set the scene for subsequent chapters.
Presentation slides that accompany this chapter can be downloaded in the following formats: slides only (PDF); slides with notes (PDF, ODP, PPTX).
Video: Cryptography Concepts and Terminology mini-lecture (14 min; Feb 2020)
2.1 Security Concepts
There are three broad protections that are considered important when securing information systems:
- Confidentiality
- ensures only authorised parties can view information
- Integrity
- ensures information, including identity of sender, is not altered
- Availability
- ensures information accessible to authorised parties when needed
Examples of confidentiality: a file is encrypted so that only authorised party (with a secret key) can decrypt to read the contents of the file; web traffic sent across Internet is encrypted so that intermediate users cannot see the web sites and content of web pages you are visiting.
Examples of integrity: If someone maliciously modifies a message, the receiver can detect that modification; if someone sends a message pretending to be someone else, the receiver can detect that it is a different person.
Examples of availability: a web server provides customers ability to buy products; that web server is available for the customers 24/7 even under malicious attacks.
While Confidentiality, Integrity and Availability (CIA) is commonly referred to, it does not cover everything. There are other classifications of protections. Often Authentication, Authorisation and Accounting (AAA) is also referred to as additional protections.
- Authentication
- ensures that the individual is who she claims to be (the authentic or genuine person) and not an impostor
- Authorisation
- providing permission or approval to use specific technology resources
- Accounting
- provides tracking of events
Example of authentication: check username and password when user logs into system.
Example of authorisation: check that user is authorised to access a particular document.
Example of accounting: record logs of who accesses files and provide summary reports.
This book does not attempt to cover everything. The scope is:
- Focus on confidentiality and integrity of information using technical means
- Means of authentication also covered
- Accounting, system availability, policy, etc. are out of scope
- See other subjects or books on “IT Security”, “Network Security Concepts” or similar
2.2 Cryptography Concepts
Encryption is a key mechanism in cryptography, and often used to provide confidentiality.
- Aim: assure confidential information not made available to unauthorised individuals (data confidentiality)
- How: encrypt the original data; anyone can see the encrypted data, but only authorised individuals can decrypt to see the original data
- Used for both sending data across network and storing data on a computer system
While encryption is used to provide different services in cryptography, the main service is confidentiality: keeping data secret. In the following we talk about using encryption for confidentiality. Later we will see that the same encryption mechanisms can also provide other services such as authentication, integrity and digital signatures.
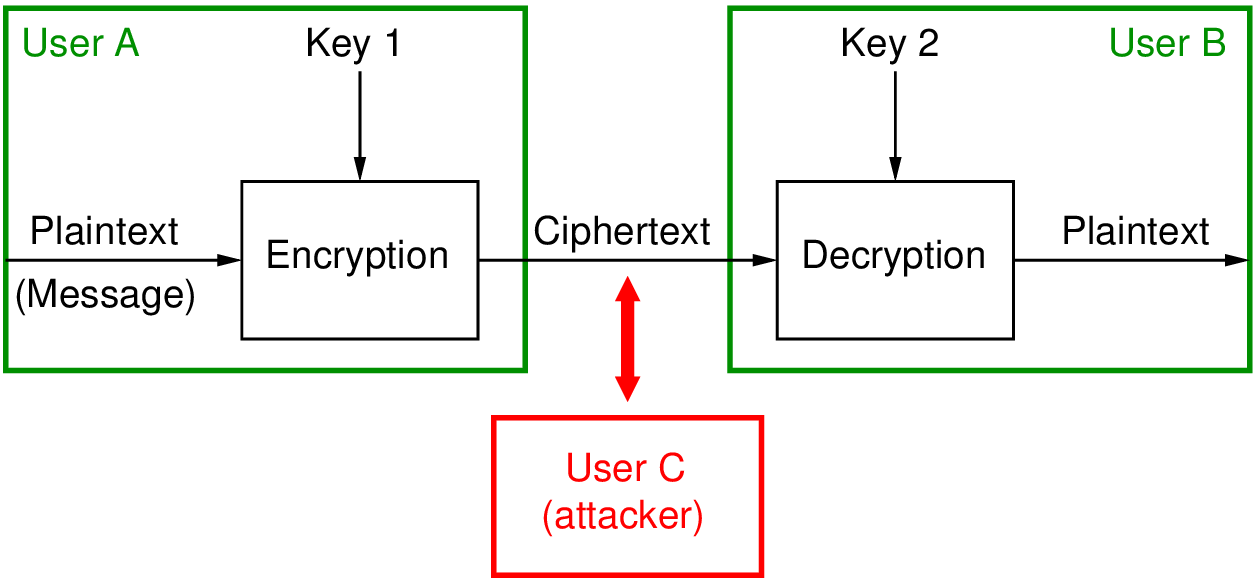
Figure 2.1 shows a simple model of system that uses encryption for confidentiality. Assume two users, A and B, want to communicate confidentially. User A has a plaintext message to send to B. User A first encrypts that plaintext using a key. The output ciphertext is sent to user B (e.g. across the Internet). We assume the attacker, user C, can intercept anything sent – in this case they see the ciphertext. User B receives the ciphertext and decrypts. If the correct key and algorithm is used, then the output of the decryption is the original plaintext.
The aim of the attacker is to find the plaintext. They can either do some analysis of the ciphertext to try to discover the plaintext, or try to find the key (if the attacker knows key 2, they can decrypt the same as user B).
In symmetric key crypto, Key 1 and Key 2 are identical (symmetry of the keys).
In public key crypto, Key 1 is the public key of B and Key 2 is the private key of B. (asymmetric of the keys).
Given the above scenario, the important terms in cryptography are:
- Plaintext
- original message
- Ciphertext
- encrypted or coded message
- Encryption
- convert from plaintext to ciphertext (enciphering)
- Decryption
- restore the plaintext from ciphertext (deciphering)
- Key
- information used in cipher known only to sender/receiver
- Cipher
- a particular algorithm (cryptographic system)
- Cryptography
- study of algorithms used for encryption
- Cryptanalysis
- study of techniques for decryption without knowledge of plaintext
- Cryptology
- areas of cryptography and cryptanalysis
2.3 Cryptography Notation and Terminology
Mathematical notation is often used when describing cryptographic mechanisms, as it is precise and brief. Table 2.1 summarises the main notation used in this book. For brevity, single letters are often used to refer to information or operations. However sometimes we need to change the letter to avoid ambiguity. For example, often refers to plaintext. However in public key cryptography we see the letter P used in the public key () and private key (), and so use to refer to the plaintext (or message).
Operations, such as encryption, decryption and hashes, are written as functions, where the inputs to the operation are given as parameters within parentheses, and the output of the operation is assigned to the variable to the left of the equal sign. For encryption and decryption, the inputs are commonly order as key then data (plaintext or ciphertext).
Subscripts are often used to identify either the information belongs to a particular user or that the operation uses a specific algorithm. For example, is a private key that belongs to user A, and is a secret key shared between users X and Y. means apply a hash function, specifically the MD5 algorithm.
| Symbol | Description | Example |
| Plaintext or message | ||
| Message or plaintext | ||
| Ciphertext | or | |
| Secret key, symmetric key | ||
| Secret key shared between A and B | ||
| Encrypt operation | or | |
| Encrypt operation using cipher | ||
| Decrypt operation | or | |
| Public key of user A | ||
| Private key of user A | ||
| Hash operation | ||
| MAC operation | ||
| , | Exclusive OR operation | , |
| Hash value | ||
| Concatenate (join) operation | ||