Chapter 11
Block Cipher Modes of Operation
11.2 Electronic Code Book
11.3 Cipher Block Chaining Mode
11.4 Cipher Feedback Mode
11.5 Output Feedback Mode
11.6 Counter Mode
11.7 XTS-AES
This chapter presents common modes of operation available with symmetric block ciphers. Modes of operation allow the block ciphers to be applied to inputs greater than the block size. The difference in designs lead to different security and performance tradeoffs. This chapter is primarily for reference, presenting the modes but with little explanation of each.
Presentation slides that accompany this chapter can be downloaded in the following formats: slides only (PDF); slides with notes (PDF, ODP, PPTX).
11.1 Block Ciphers with Multiple Blocks
Block ciphers operate on fixed length inputs, so the question arises of how are they used to encrypt arbitrary length inputs?
- Block cipher: operates on fixed length -bit input to produce -bit ciphertext
- What about encrypting plaintext longer than bits?
- Naive approach: Break plaintext into -bit
blocks (padding if necessary) and apply cipher on each block independently
- ECB
- Security issues arise:
- Repetitions of input plaintext blocks produces repetitions of output ciphertext blocks
- Repetitions (patterns) in ciphertext are bad!
- Different modes of operation have been developed
- Tradeoffs between security, performance, error handling and additional features (e.g. include authentication)
We will not cover each mode of operation in detail, but rather present them so you are aware of some of the common modes. For more technical details of some of these modes of operation, including discussion of padding, error propagation and the use of initialisation vectors, see NIST Special Publication 800-38A Recommendations for Block Cipher Modes of Operation: Methods and Techniques. Additional (newer) modes of operation are in the NIST SP 800-38 series, such as 800-38C CCM, 800-38D GCM and 800-38E XTS-AES.
11.2 Electronic Code Book
Figure 11.1 and Figure 11.2 show the Electronic Code Book (ECB) mode of operation applied for encryption and decryption, respectively.
- Each block of 64 plaintext bits is encoded independently using same key
- Typical applications: secure transmission of single values (e.g. encryption key)
- Problem: with long message, repetition in plaintext may cause repetition in ciphertext
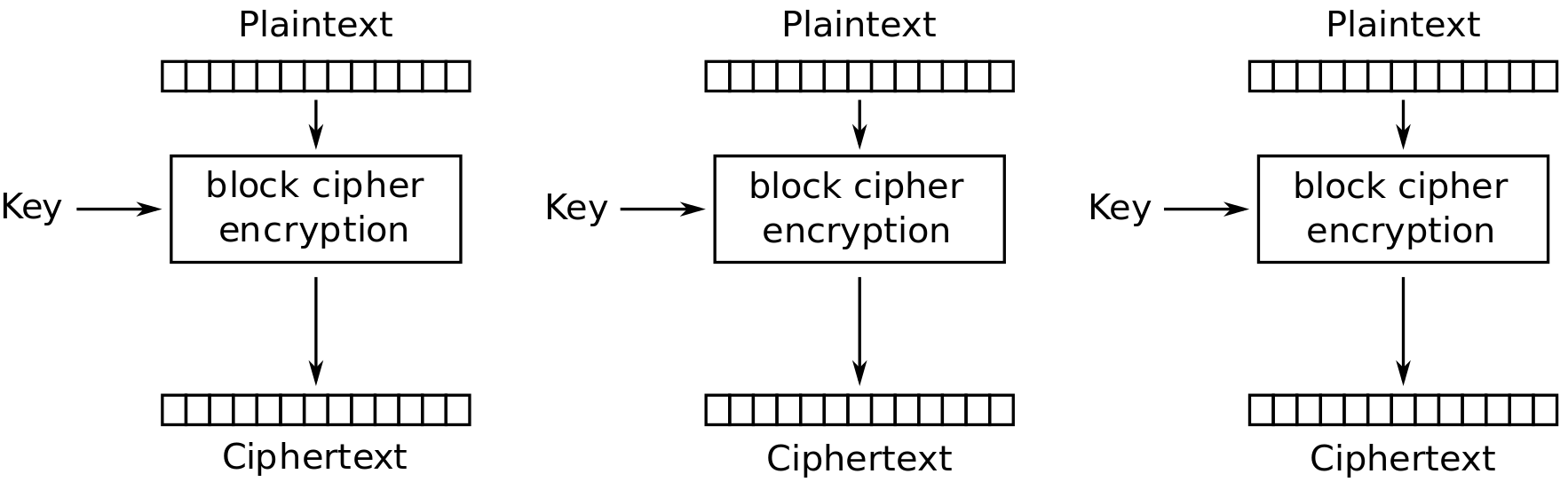
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:ECB_encryption.svg, public domain
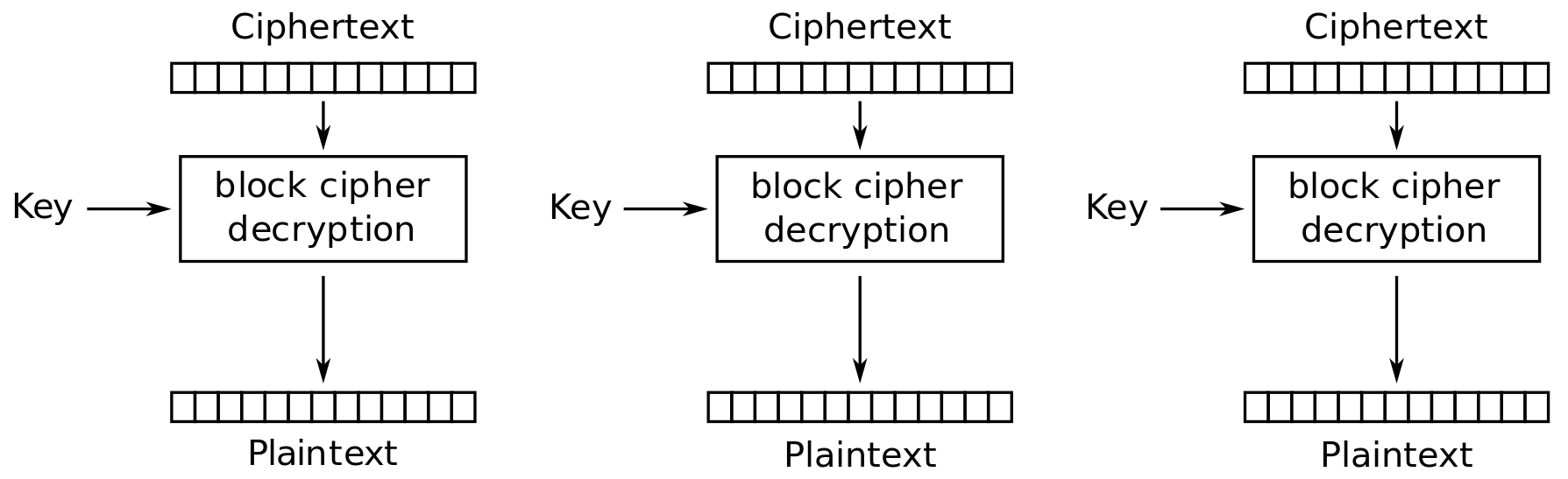
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:ECB_decryption.svg, public domain
11.3 Cipher Block Chaining Mode
Figure 11.3 and Figure 11.4 show the Cipher Block Chaining (CBC) mode of operation applied for encryption and decryption, respectively.
- Input to encryption algorithm is XOR of next 64-bits plaintext and preceding 64-bits ciphertext
- Typical applications: General-purpose block-oriented transmission; authentication
- Initialisation Vector (IV) must be known by sender/receiver, but secret from attacker
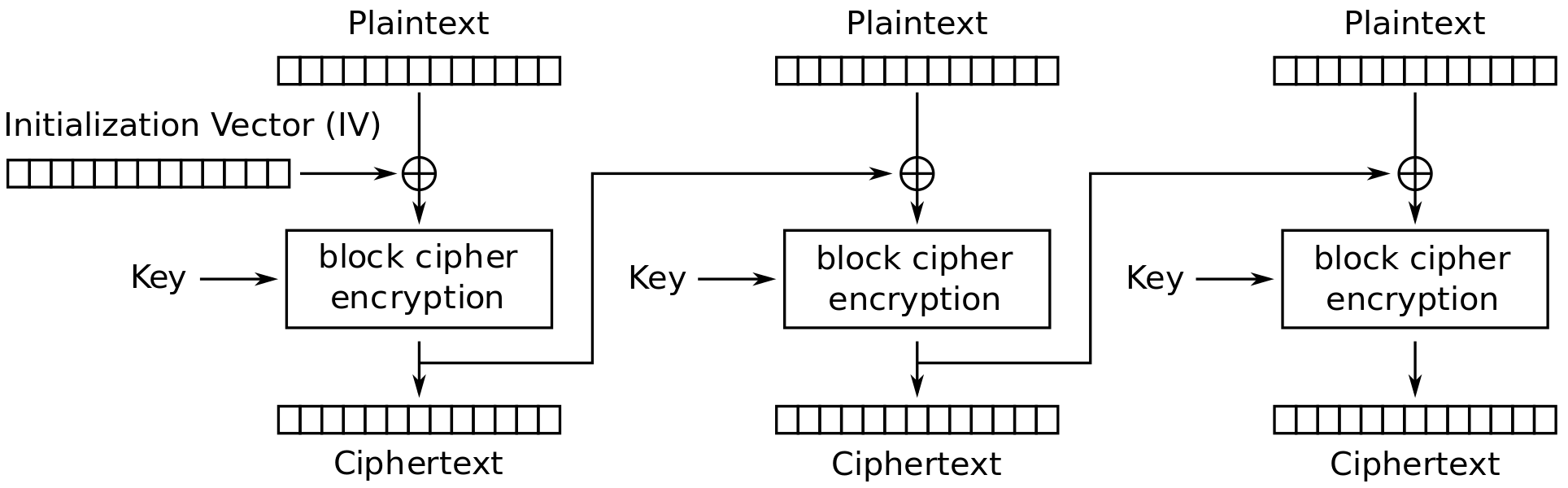
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CBC_encryption.svg, public domain
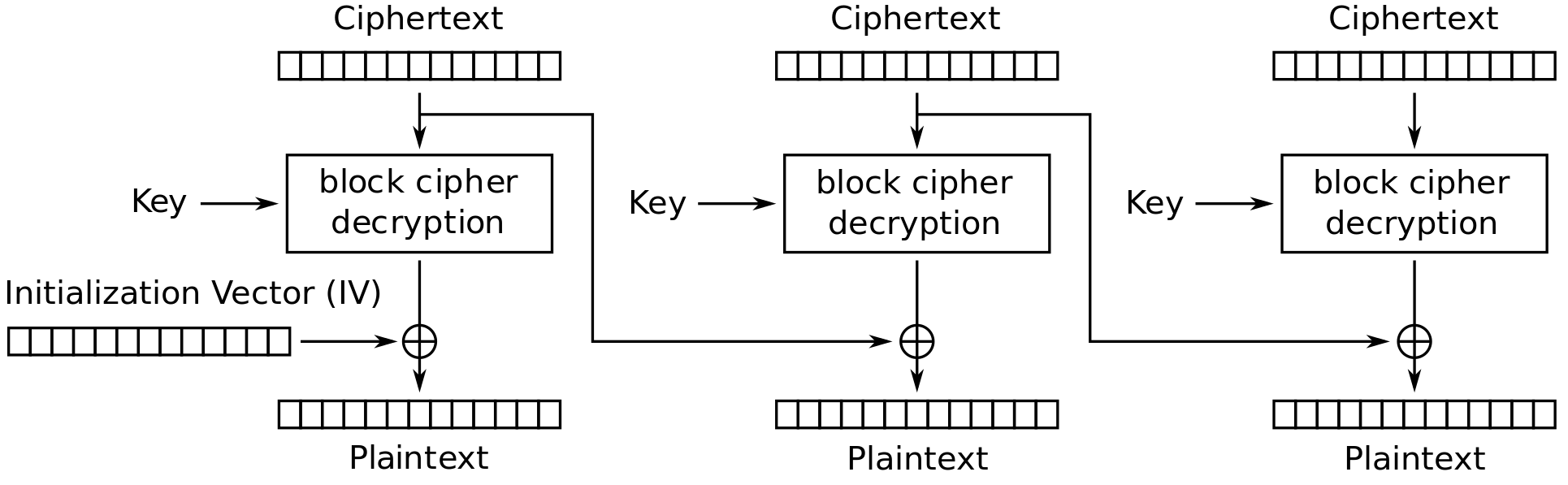
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CBC_decryption.svg, public domain
11.4 Cipher Feedback Mode
Figure 11.5 and Figure 11.6 show the Cipher Feedback mode (CFB) mode of operation applied for encryption and decryption, respectively.
- Converts block cipher into stream cipher
- No need to pad message to integral number of blocks
- Operate in real-time: each character encrypted and transmitted immediately
- Input processed bits at a time
- Preceding ciphertext used as input to cipher to produce pseudo-random output
- XOR output with plaintext to produce ciphertext
- Typical applications: General-purpose stream-oriented transmission; authentication
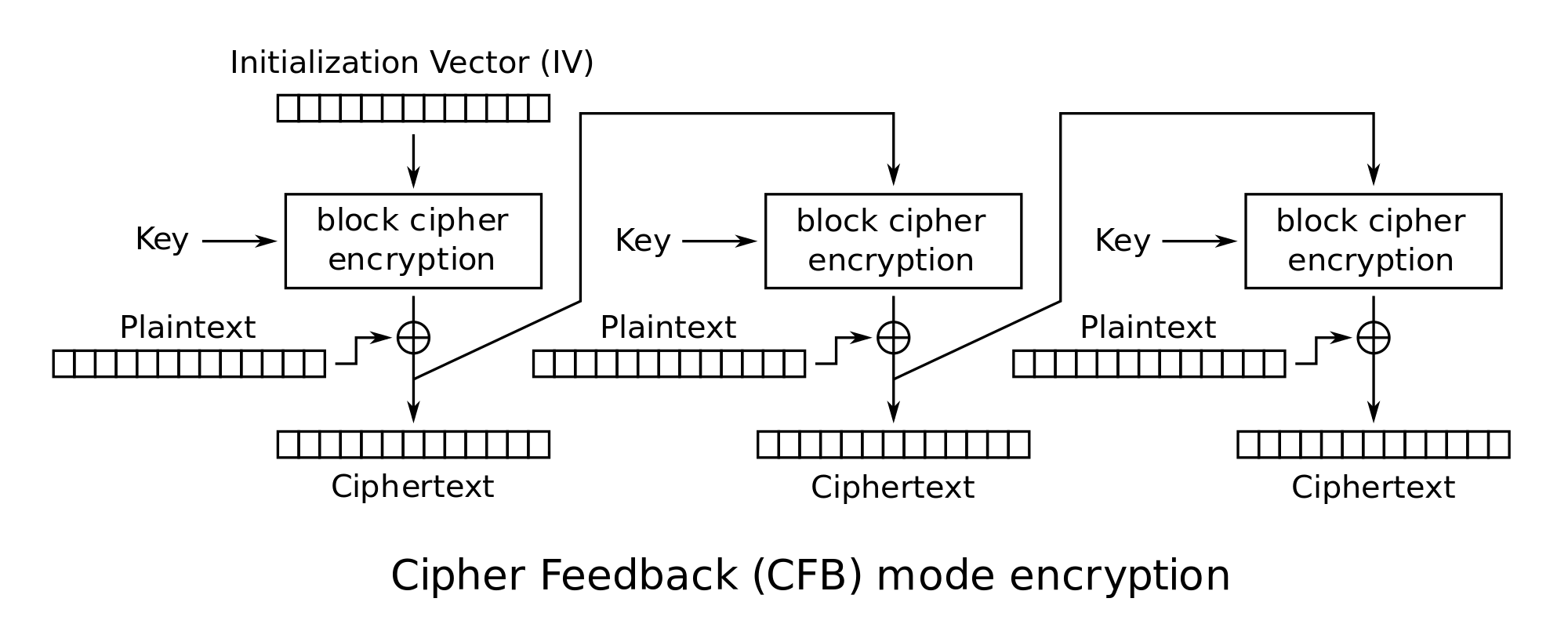
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CFB_encryption.svg, public domain
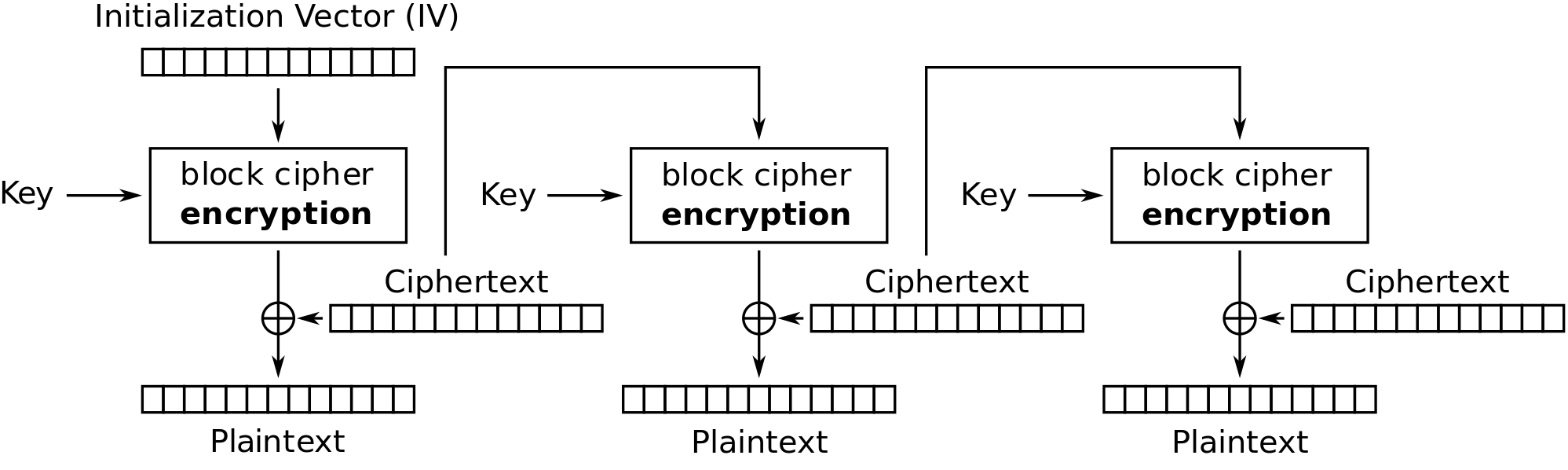
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CFB_decryption.svg, public domain
11.5 Output Feedback Mode
Figure 11.7 and Figure 11.8 show the Output Feedback mode (OFB) mode of operation applied for encryption and decryption, respectively.
- Converts block cipher into stream cipher
- Similar to CFB, except input to encryption algorithm is preceding encryption output
- Typical applications: stream-oriented transmission over noisy channels (e.g. satellite communications)
- Advantage compared to OFB: bit errors do not propagate
- Disadvantage: more vulnerable to message stream modification attack
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:OFB_encryption.svg, public domain
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:OFB_decryption.svg, public domain
11.6 Counter Mode
Figure 11.9 and Figure 11.10 show the Counter mode (CTR) mode of operation applied for encryption and decryption, respectively.
- Converts block cipher into stream cipher
- Each block of plaintext XORed with encrypted counter
- Typical applications: General-purpose block-oriented transmission; useful for high speed requirements
- Efficient hardware and software implementations
- Simple and secure
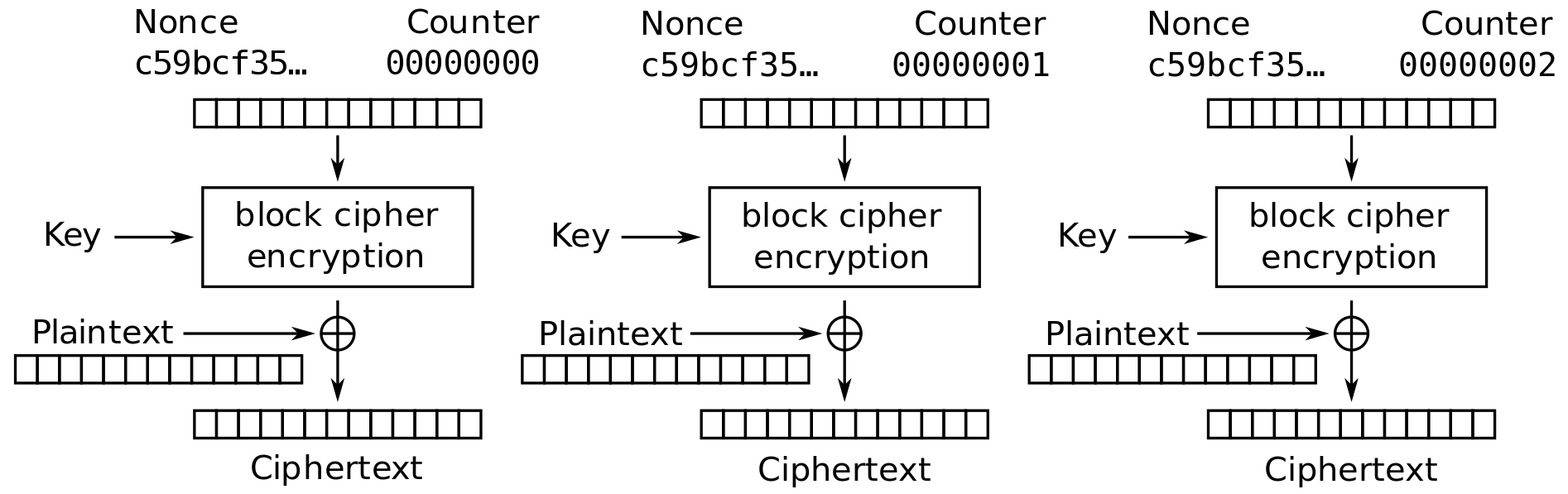
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CTR_encryption_2.svg, public domain
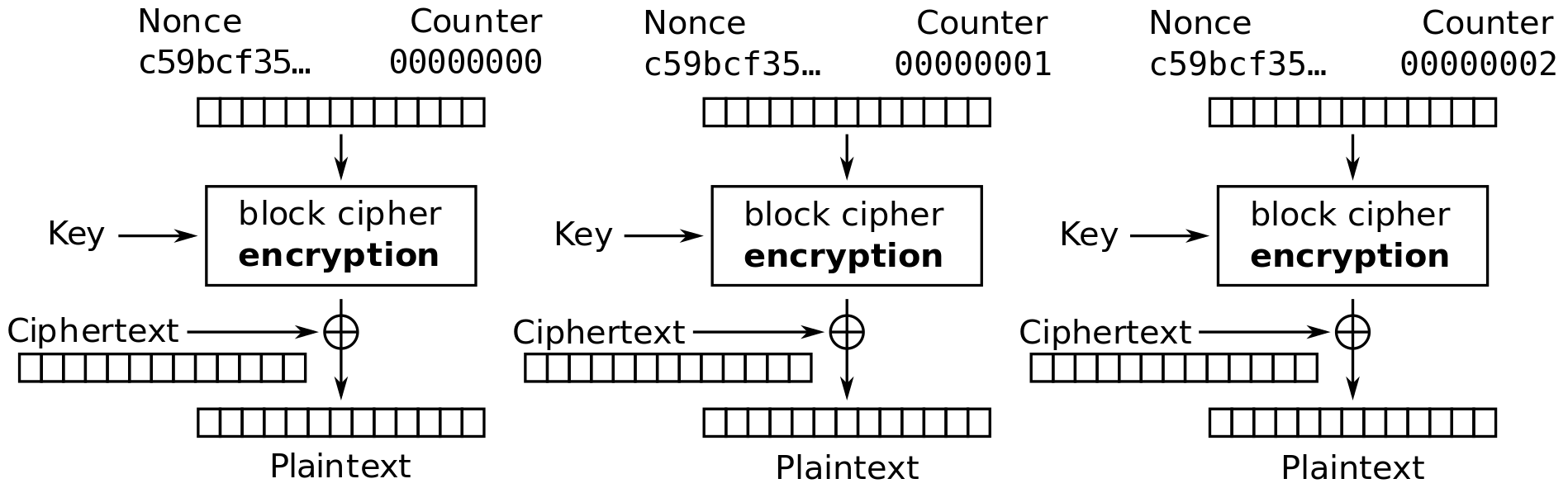
Credit: Wikimedia https://commons.wikimedia.org/wiki/File:CTR_decryption_2.svg, public domain
11.7 XTS-AES
XTS-AES is a mode of operation designed for AES to be used to encrypt stored data (e.g. disk drives). Compared to CBC, it improves the ability for a receiver to detect if the ciphertext has been changed.
- XTS-AES designed for encrypting stored data (as opposed to transmitted data)
- Overcomes potential attack on CBC whereby one block of the ciphertext is changed by the attacker, and that change does not affect all other blocks
- See Stallings Chapter 6.7 for details and differences to transmitted data encryption