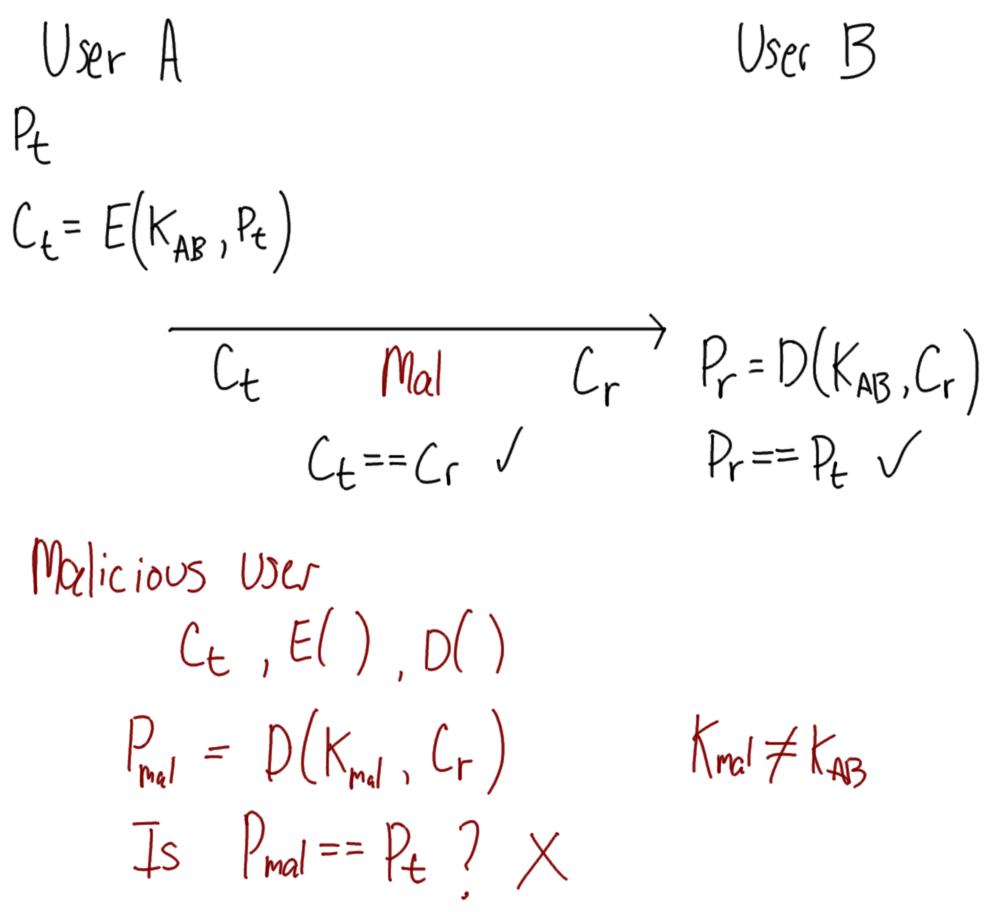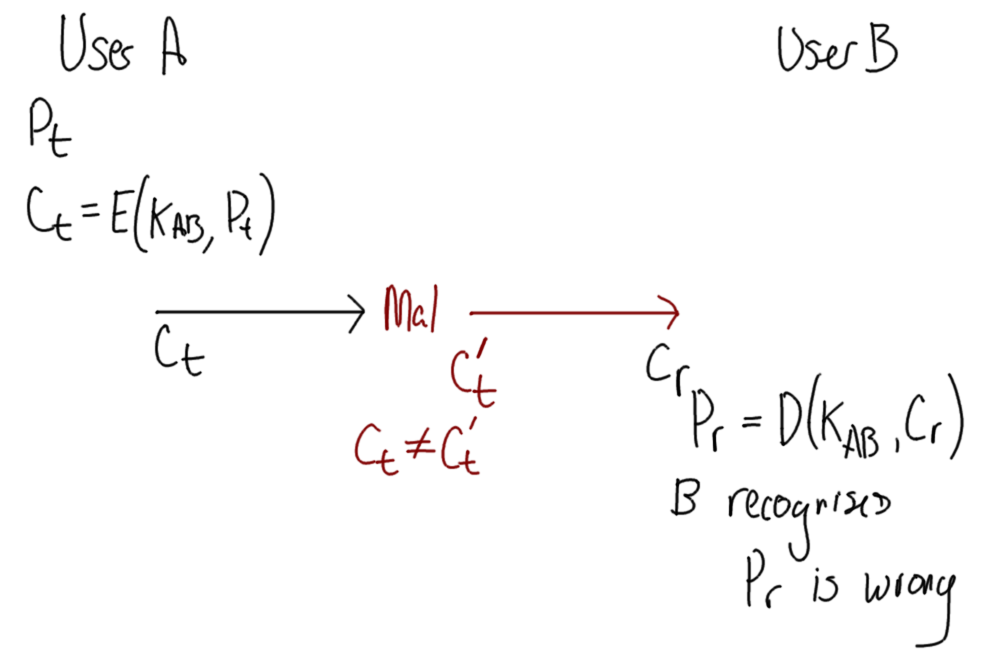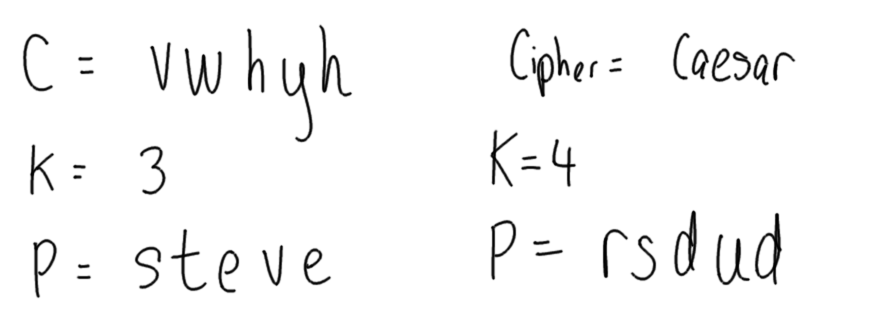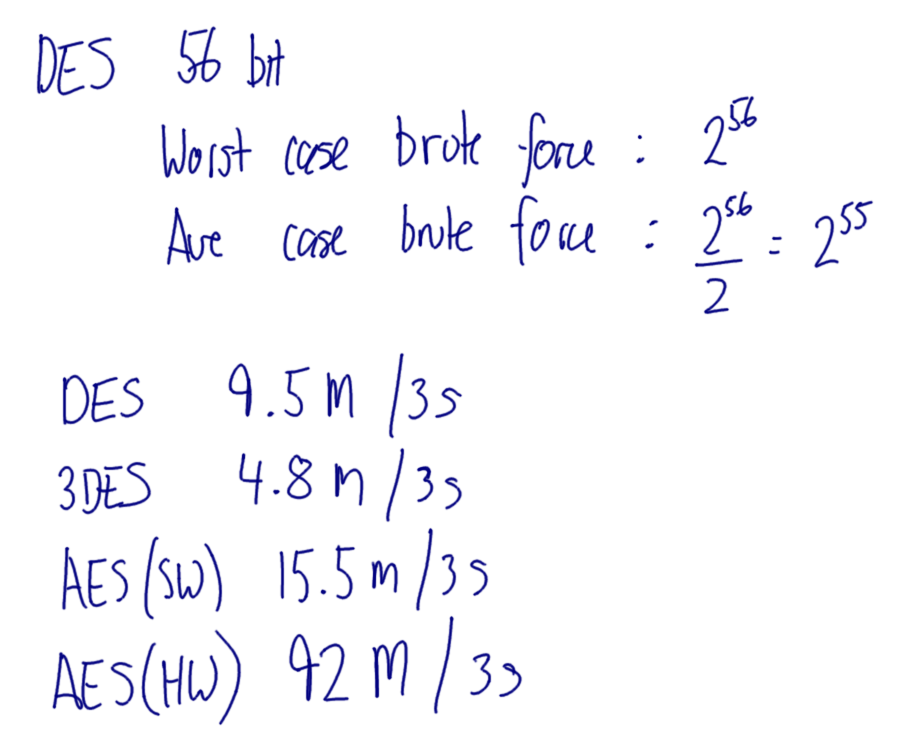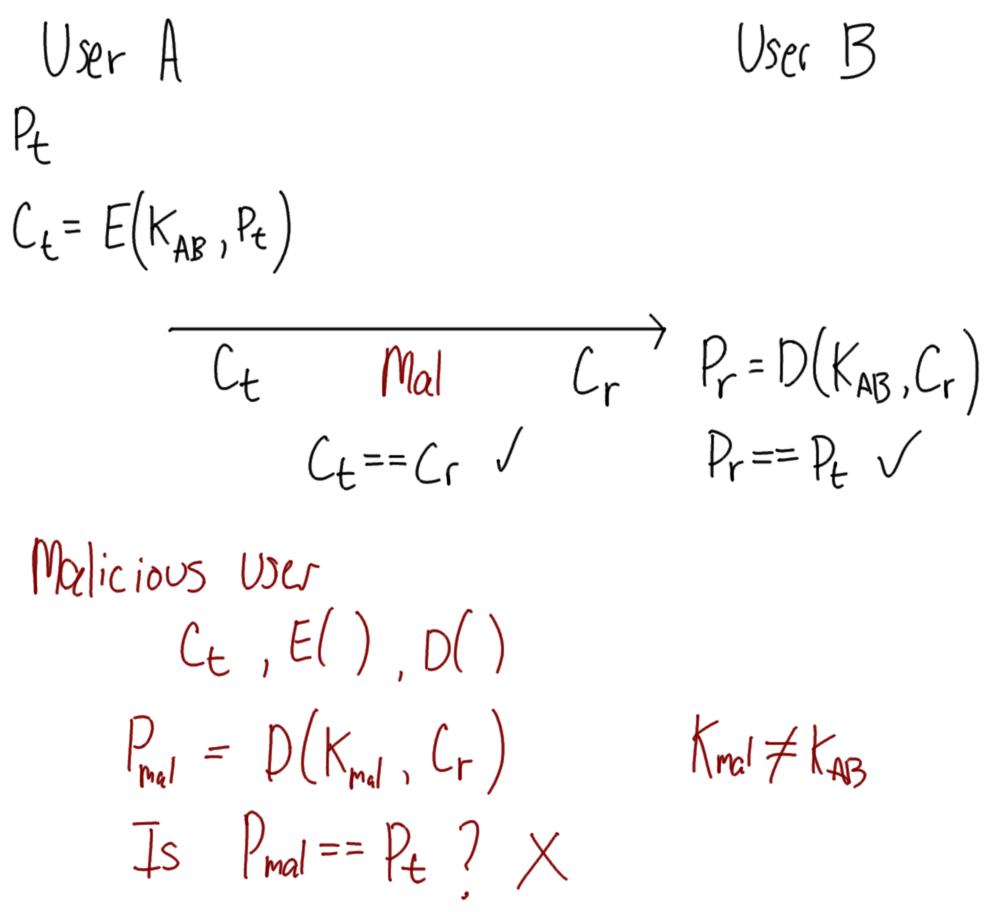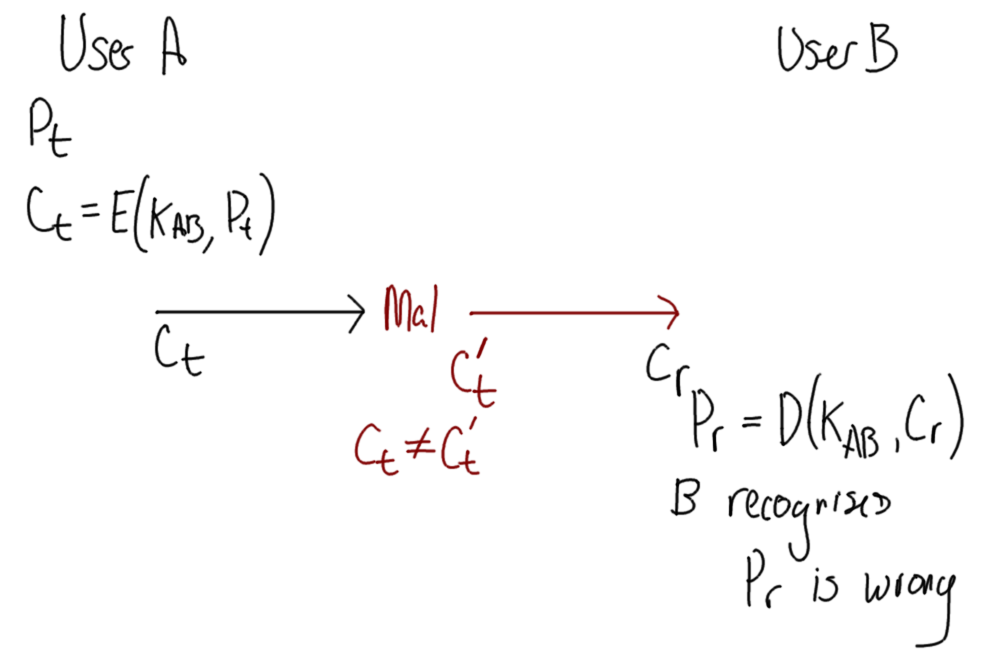IT Security (S2, 2015)
Cryptography
Lecture Material
Lecture Notes: View , Print , Source
Simple Introduction to Using OpenSSL on the Command line: View , Print
Public Key Encryption and Digital Signatures using OpenSSL: View , Print
Brute Force of DES and AES: View , Print
Cryptography Assumptions and Principles Summary: View , Source
Readings
Computer Security by Stallings and Brown: chapter 2, (20, 21)Cryptography and Network Security by Stallings: chapter 2, 3, 7, 9, 11, 12, 13, 14Network Security by Kaufman, Perlman and Speciner: chapter 2, 3, 4, 5, 6Cryptography and Network Security by Forouzan: chapter 5, 6, 10, 11, 12Security Engineering by Anderson: chapter 5Handbook of Applied Cryptography by Menezes, van Oorschot and Vanstone: chapter 1 (entire book)
Videos
VIDEO
VIDEO
VIDEO
VIDEO
Notes
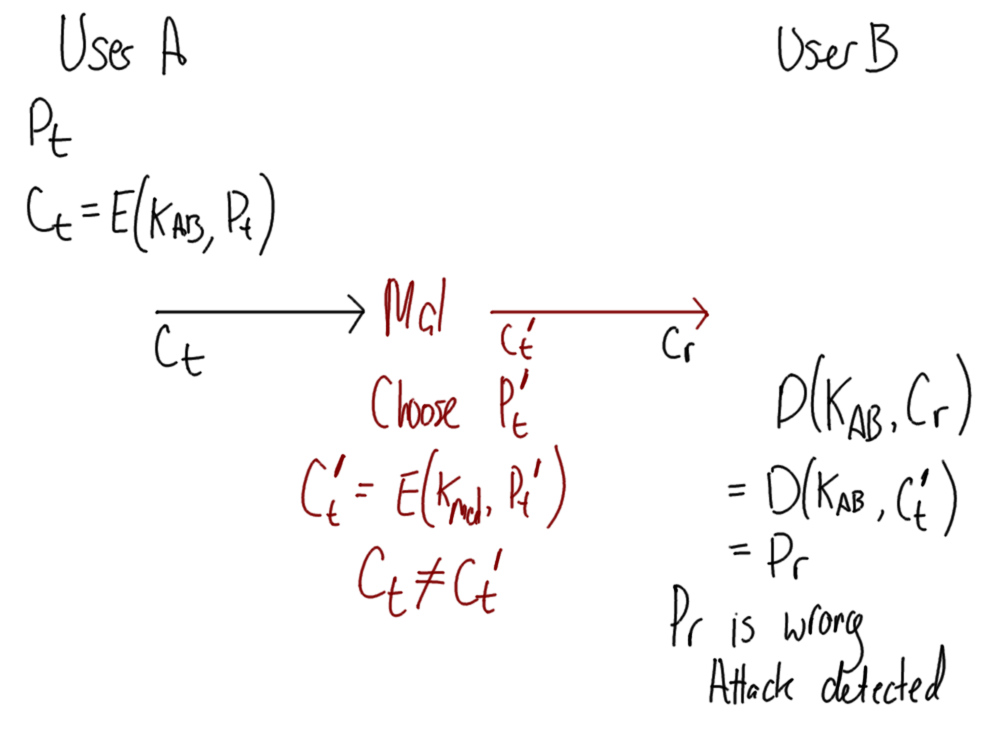
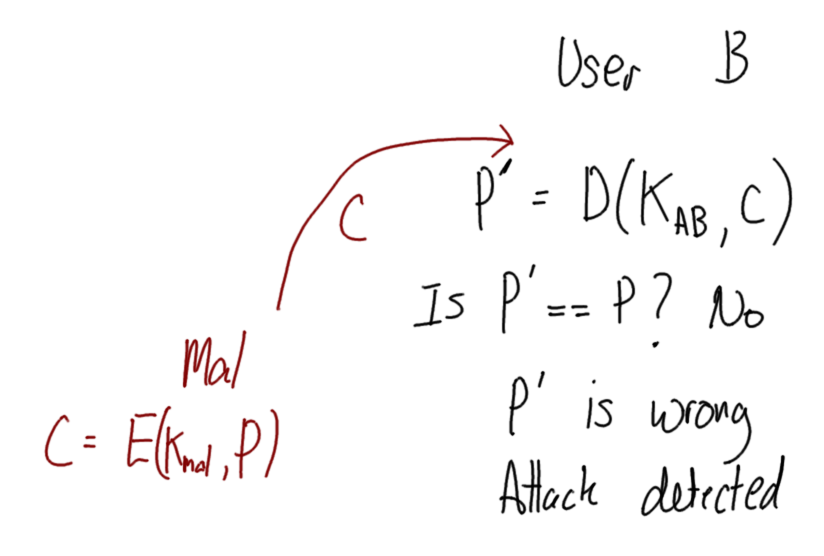
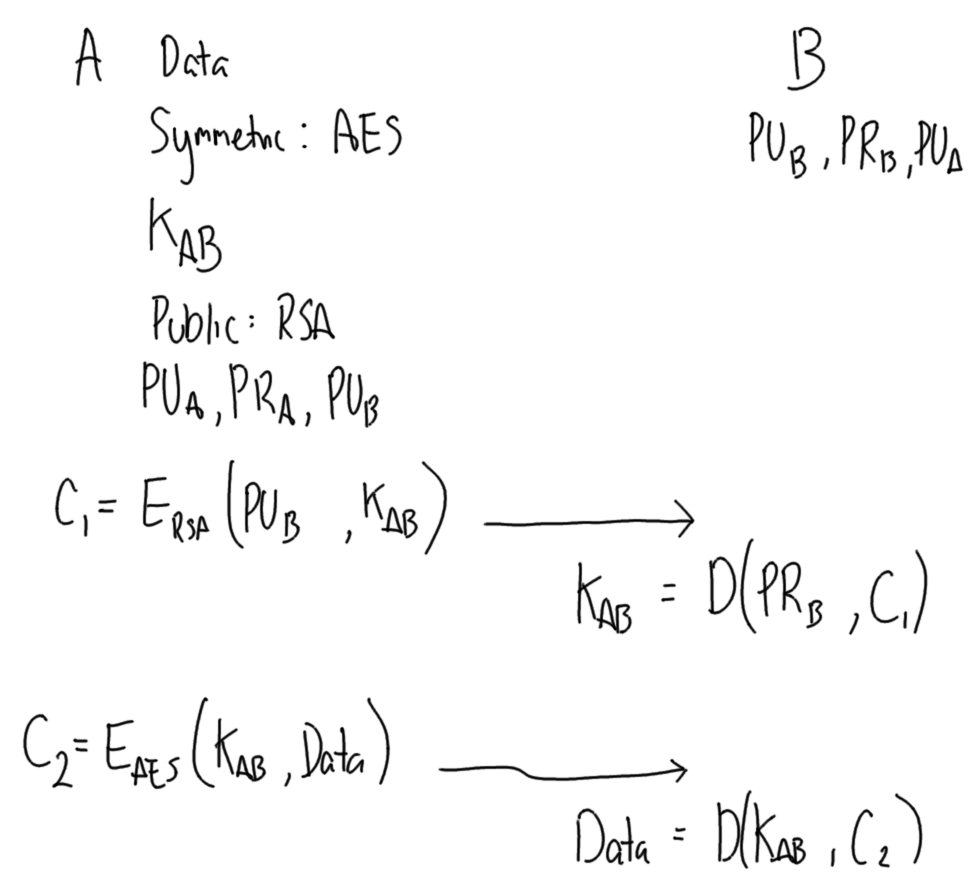
Hover over images to see the title; right-click and view the image to zoom in. Alternatively, download a zip archive with all the images or a printable PDF of the notes. You can also download a printable PDF of the notes from last year.
Return to: Course Home | Course List | Steven Gordon's Home | SIIT